About
Who we are
At Acutiv, we epitomize the future of cybersecurity consultation and advisory. In a landscape often cluttered with static approaches and outdated tools, we emerge as the vanguard of change, pioneering dynamic, personalized strategies tailored to meet the unique needs of each organization. Our mission is clear: to empower businesses, regardless of size or industry, to navigate the complexities of cybersecurity with unwavering confidence.
- Advisory services blending human expertise with technological innovation.
- Features including current state assessment, target-state definition, and rapid maturity analysis.
- Unified Managed Security Services to helping clients secure themselves against evolving cyber threats.
By democratizing cybersecurity, we level the playing field, enabling organizations to thrive securely in the digital age.
Our vision extends beyond securing networks and data; it encompasses a commitment to equipping our clients with the knowledge, tools, and training necessary to co-create and innovate, fortifying themselves against the ever-evolving cyber threat landscape.
At Acutiv, we're not just securing systems; we're empowering futures.
Learn More
A new generation of cyber threats leveraging AI technology.
These threats might exploit AI algorithms to automate attacks, create sophisticated phishing campaigns, or bypass security measures through intelligent evasion tactics. Additionally, they could utilize AI to analyze vast amounts of data quickly, allowing them to identify vulnerabilities and launch targeted attacks with greater precision and efficiency.
- Automated Malware
- Advanced Phishing
- Targeted Attacks
- Insider Threats
To combat the emerging threat landscape associated with AI-powered cyberattacks, Acutiv has developed advanced cybersecurity strategies. This includes correlating AI-driven threat detection systems, enhancing employee training to recognize AI-generated threats, and continuously updating security protocols to stay ahead of evolving cyber threats.
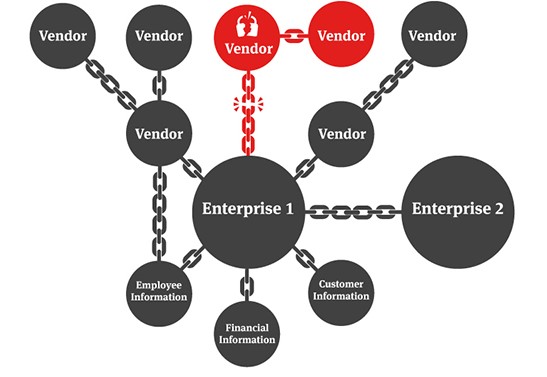
Supply Chain Threats
Risks and vulnerabilities that can arise from the interconnected network of suppliers, vendors, manufacturers, distributors, and other entities involved in delivering goods or services to an organization. These threats can compromise the integrity, confidentiality, availability, or quality of products or services, leading to significant financial, operational, and reputational damage.
Common types of supply chain threats include:
- Intellectual Property Theft
- Counterfeit Products
- Data Breaches
- Supply Chain Disruptions
To mitigate supply chain threats, Acutiv has been assisting organizations to implement robust risk management strategies, including supply chain visibility, vendor assessment and monitoring, contractually binding security requirements, diversification of suppliers, contingency planning, and incident response preparedness.
Ransomware Threats
Ransomware attacks are a form of malicious cyber activity where attackers encrypt an organization's data or systems and demand a ransom payment in exchange for restoring access. Ransomware attacks pose significant risks to organizations, including financial losses, operational disruptions, reputational damage, and potential data breaches.
These attacks typically involve the following stages:
- Infection
- Encryption
- Ransom Demand
- Negotiation and Payment
- Data Recovery
To mitigate these risks, Acutiv assists organizations to implement robust cybersecurity measures, including regular data backups, endpoint security solutions, email filtering, employee training and awareness programs, vulnerability management, and incident response plans.

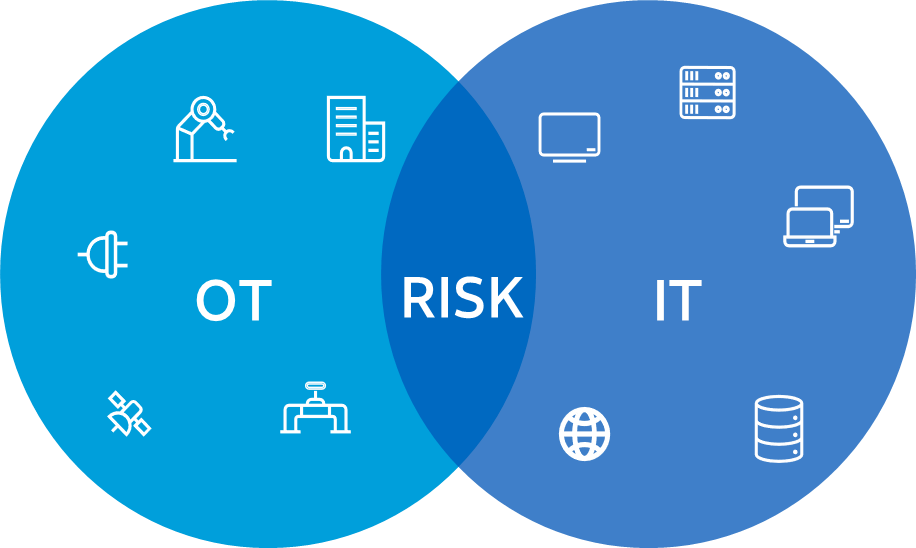
Information Technology (IT) - Operational Technology (OT) Convergence
While this integration between IT and OT offers benefits like improved efficiency and productivity, it also introduces new cybersecurity challenges and risks.
Here's a summary of IT-OT convergence threats:
- Cyber-Physical Attacks
- Ransomware Targeting OT Systems
- Supply Chain Risks
- Legacy System Vulnerabilities
- Insider Threats
- Regulatory Compliance Challenges
To address these threats, organizations should implement comprehensive cybersecurity strategies tailored to the unique characteristics of their IT-OT environments.
This includes conducting risk assessments, deploying specialized security solutions for OT systems, establishing network segmentation and access controls, enhancing incident detection and response capabilities, fostering collaboration between IT and OT teams, and investing in employee training and awareness programs focused on cybersecurity best practices for industrial environments.
Call To Action
The time to take proactive steps in securing your organization's future is now. Don't wait until it's too late to safeguard your assets from evolving cyber threats. Reach out to us today to embark on your journey towards enhanced cybersecurity resilience.
Services
What we do offer
CGRC: Cybersecurity Goverance, Risk & Compliance
Acutiv introduces a comprehensive Cybersecurity Governance, Risk, and Compliance (GRC) solution and services designed to streamline and fortify organizations' cybersecurity strategies.
PCIS: Physical. Cloud and Infrastructure Security
Physical, Cloud, and Infrastructure Security services, redefining the paradigm of protection across digital and physical domains.
IDAS: Identity, Data, and Application Security
A robust Identity, Data, and Application Security solution and services, revolutionizing the protection of critical assets and systems in the digital realm.
CSNOC: Cognitive Security & Network Operations Center
A revolutionary Cognitive Security Operations Center (SOC), ushering in a new era of proactive threat detection and response.
TTM: Tactical Threat Management
Acutiv offers advanced Security Incident Response, Penetration Testing, Vulnerability, and Threat Management services, providing organizations with comprehensive assessments of their cybersecurity defenses.
UMSS: Unified Managed Security Services
We offer state-of-the-art secure, unified and fully automated managed security services across all our competencies.
Team
Our Hardworking Team

Mehmoud S.
Chief Executive Officer
Ahsan Kamal
Strategic Accounts Director
Bilal Khalid
Business Communications Director
Shahid Khan
MEA Regional Sales LeaderInquire
Contact Us
Location:
Office 1062
Building B2, Floor 1
Dubai CommerCity
Dubai, UAE
Email:
info@acutiv.com
Call:
+971-56-664-7606
+971-58-696-1183
